Know More about Foxy
- ITSC User Satisfaction and Needs Survey 2021
- Closing of User Area on 26 Mar 2021 (2:00PM – 6:00PM)
- Phishing Alert: Follow Up Email Immediately
- SPSS and AMOS License Server Maintenance for Application Upgrade on 25 Apr
- Phishing Alert: Team Meeting (March)
Know More about Foxy
1. Recent incidents in related to Foxy
- Case 1: Another data leak prompts security vow, 9 May 2008
- Case 2: Covert cops hit by leaks, 27 May2008
2. Features and characteristics of Foxy
- It is a kind of Peer-to-peer (P2P) software to facilitate file sharing, like BitTorrent and eMule.
- It supports mainly two functions which are ‘search’ and ‘download’.
- Its user interface is in Traditional Chinese and is famous to be user friendly
- It is popular in Hong Kong, Mainland and Taiwan.
3. FAQs:
- How can I know if my computer has Foxy installed?
A: If Foxy has been installed in your computer, you will find:
I. The Foxy icon from Windows Program list and in the program bar
from Windows Program list and in the program bar
 II. An installation directory C: \Program Files\Foxy
II. An installation directory C: \Program Files\Foxy
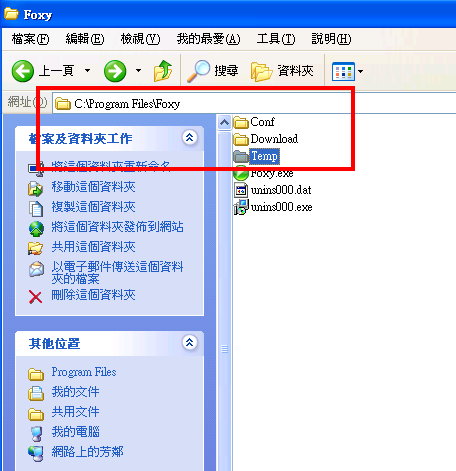
- How to uninstall Foxy?
A.: Follow the following 3 Steps:
Step 1: Click ‘Uninstall Foxy’ in the program bar.
Step 2: Erase the directory and all files under the installation directory C:\Program Files\Foxy
Step 3: Remove all entries added by Foxy in the exception list of Windows Firewall.

- Once a file is shared, can it be stopped?
No, it can’t be stopped.? The file would be copied to the requestors’ computer afterdownload and you won’t know who the requester is. - Can owner of a file be identified and traced?
No, Foxy won’t show the identity of the source who shares the file.
4. Possible causes of the recent incidents:
- Installing Foxy from an unofficial website.
Some unofficial websites claim that they had “enhanced” version Foxy which supports faster downloading speed. However, this “enhanced” version of Foxy may contain backdoors inserted by hackers to share all files in your computer automatically without your notice. - Misconfiguration
- Some cases of unintentional file sharing are due to the following unaware features of Foxy:
Features Implication Auto-startup By default, Foxy starts up automatically after login. Download folder The “Download folder” is compulsorily shared. Share folder By default, all sub-folders and files under “Share Folder” are shared. - Inherited setting: The Foxy settings are inherited to users sharing the same computer and this may lead to unintentional information leakage. For example, your kid at home may set to share the music files in a USB drive through Foxy and this setting would inherit to you when you use the same computer. So, when you plug in your USB drive to read sensitive files inside, Foxy will share these files to others without your awareness.
- Some cases of unintentional file sharing are due to the following unaware features of Foxy:
- Infection of virus or worm.
If your computer is infected by virus or worm, the Foxy settings could be changed without your notice. The following are two popular P2P software worms and their effects:
Virus / Worm Effect TROJ_GNUTELMAN.A Inflected computers easily become overloaded. PE_POLIP.A - It consumes a large amount of system resources and causes the victim’s computer to become noticeably sluggish and unreliable.
5. Suggested preventions:
- Follow the good practice:
- Uninstall software if you don’t need it.
- Turn off unnecessary software like Foxy after use.
- Check and make sure the Foxy is not running before you use the computer.
- Never share a pluggable drive because you may not aware what you have shared next time when you plug another drive to your computer.
- Don’t save sensitive and restricted files in local computer or any removable media. However, if it is necessary, please do
- Encryption
- Configure your computer carefully and make sure not to share any sensitive and restricted files.
- Scan all downloaded filed by antivirus and antispyware before use.
- Install security software with update security patches and scan the computer regularly.
- Download Foxy from the official site.
- If Foxy is needed, make sure you download Foxy from the official website.
- If you are not sure whether the Foxy in your computer is downloaded from the official website, you should uninstall it.
- Separate user accounts in a shared computer.
Separate user accounts in a shared computer and assign no administrator right to the accounts. Although this cannot completely solve the problem of inherited settings, this can create a more personalized environment for creating personal folders for downloading and sharing files. This can lower the risk of information leakage. - Use anti-virus and anti-spyware to scan and remove inflected files
- Configure Foxy properly – If you’ve installed Foxy from the official website, you should configure it properly
- Folder setting: Assuming that you have opened separate user accounts in a shared computer, it is suggested to create three directories specifically for Foxy under each user’s “My Documents”
Directory Suggested location How to apply this setting Share My Documents \Foxy\Foxy_Share Select the folder under the tab of 共享 Download My Documents\Foxy\Foxy_download Select 下載資料夾 under 選項 Temporary My Documents\Foxy\Foxy_temp Select 暫存資料夾 under 選項 - Program setting: Disable automatic startup by unchecking ‘開機時啟動’ under the icon of 選項

- Folder setting: Assuming that you have opened separate user accounts in a shared computer, it is suggested to create three directories specifically for Foxy under each user’s “My Documents”

